In the last part of this series, we looked at the concept of sending secured messages through insecure channels of communication. In this final part of our “What Exactly is SSH?” series, we will look at software tools that make it possible to send secured messages through insecure channels of communication.
Automating the Process of Sending Secure Messages Through the Postal System
Let’s return to our postal model once again. You have a message you would like to send through the postal system (which is by nature public). You want the contents of your message to be private as the post card you wrote the message on makes its way through a public postal system.
Last time, we talked about scrambling up (or encoding) the text of your message before writing your message and putting your post card in the mailbox. When your post card reaches its destination, your friend unscrambles the message.
In order to make all of this happen, the following steps need to be handled:
- Write out the original message
- Scramble up (encode) the message
- Write the scrambled message on a post card
- Put the post card in the mail
- Make sure the recipient knows how to unscramble (decode) the message
- Lastly, the recipient needs to unscramble the message
Whew! That is a lot to do every time you want to send a message. This, of course, is where the tools of automation can help.
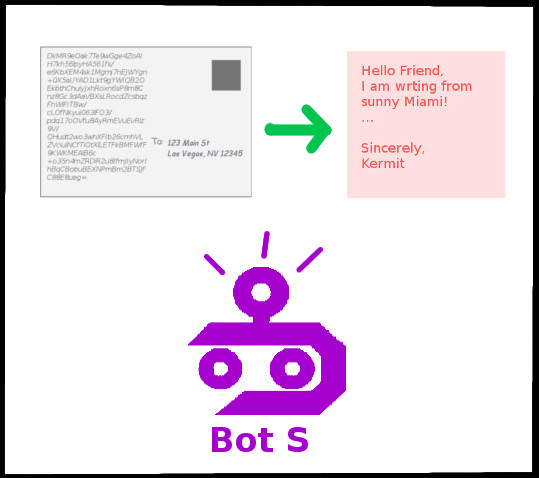
Imagine that instead of going through each of the six steps listed above, you had two helpers that took care of steps 2) through 6). Let’s call these helpers Bot C and Bot S.
As the message sender, you use Bot C, and your friend uses Bot S as the message recipient.

With the help of these bot assistants, all you need to do is give Bot C your plaintext message and where you want to send it. Bot C will scramble the message, write the message down on a post card, and mail it off for you.
Now that you have communicated the plaintext message you would like to send as well as its destination, the assistant will take care of steps 2) through 6).
Bot C will do a check to see if it knows about the bot assistant at the given address. It will only send messages to bot assistants it knows about.
Step 2: Scramble up (encode) the message
Step 3: Write the scrambled message on a post card

Step 4: Put the post card in the mail
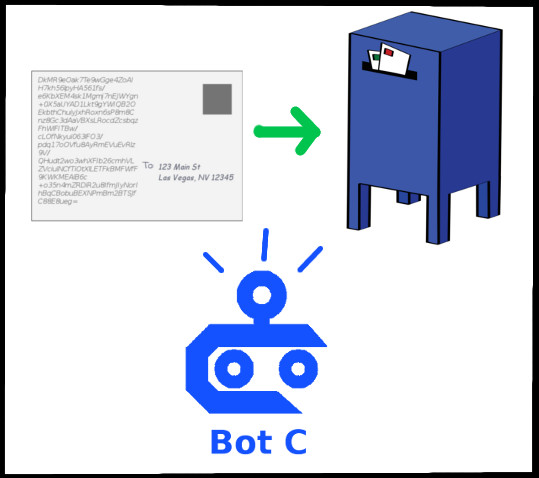
When the post card arrives at its destination, Bot S will take it, unscramble the message, and give the plaintext message to your friend.

Step 5: Make sure the recipient knows how to unscramble (decode) the message.
Bot C and Bot S were designed to work together, and Bot C already determined that it trusts Bot S. That being the case, Bot C has a way to secretly let Bot S know how to unscramble the message without giving that information away to an unintended observer.
Step 6: Unscramble the message and deliver it to the recipient
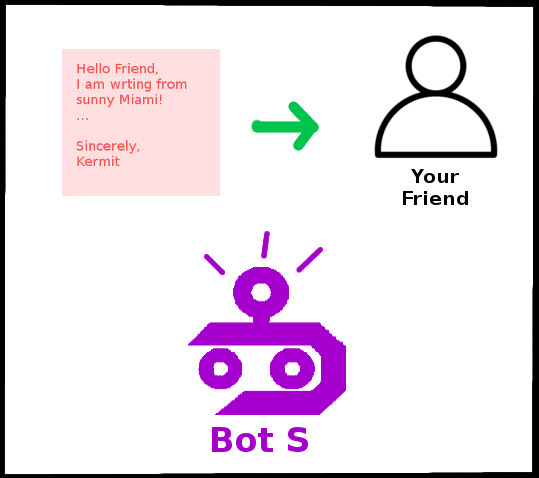
Notice that using the assistants means neither you nor your friend have to think about the process of encoding and decoding the message. All of that happens between Bot C and Bot S.
Though you and your friend only deal with plaintext messages, using the assistants allows you to rest assured that your message is secure while it travels.
Software Architecture for SSH Implementations
Remember, the SSH protocol itself is just a set of rules. In the imaginary scenario above, we used two bot assistants to implement those rules. In reality, of course, we use software to implement the SSH protocol.
Software systems that implement the SSH protocol have many different parts that must interact with each other. We will simplify things quite a bit here and look at an SSH system at a very high level.
Much like our example above with Bot C and Bot S, SSH software systems break down into a client-server architecture.
SSH Clients
Like Bot C, the client is a program that knows how to connect to SSH servers. It can send data to the server as well as request certain actions and data from the server.
Here are some examples of SSH client applications available for Linux-based systems:

SSH Servers
Bot S represents an SSH server. SSH servers are programs that know how to handle incoming connections from various SSH clients. Servers manage authentication and authorization.
Here are two examples of SSH server applications available for Linux-based systems:
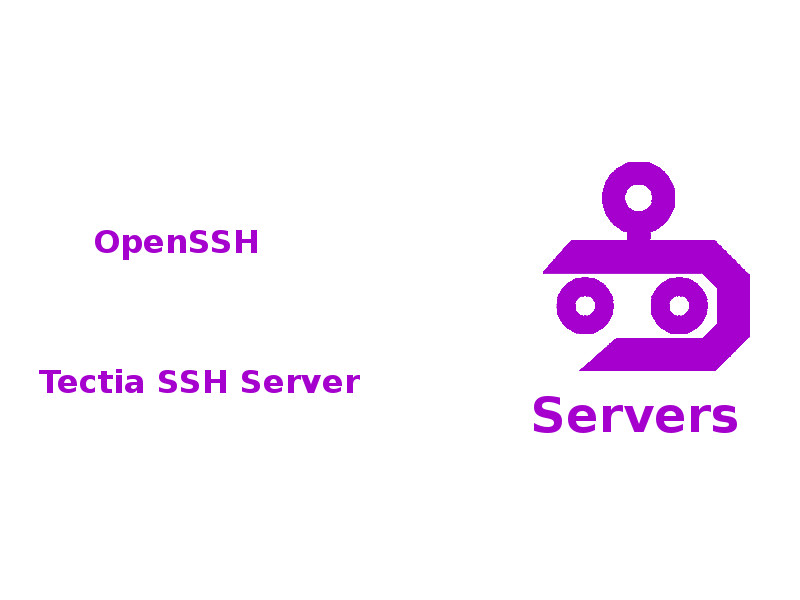
There tend to be more client application options available than server applications.
Open SSH
There are many software implementations of SSH out there, both free and paid. Now that we have a better view of the overall picture of SSH software, let’s take a look at one specific example available for Linux-based systems, OpenSSH.
The OpenSSH suite is a good example to start with because it is free, and it includes both client and server applications among other tools.
OpenSSH is a suite of tools that allow for the transfer of data as well as remote control between networked computers. We have mainly discussed file transfer and remote log in thus far, but there are other tasks that can be accomplished over a secure ssh channel. OpenSSH also supports many of these additional features, such as port forwarding (“ssh tunnelling”).
Client Side
On the client side, OpenSSH includes the ssh and sftp tools, which we used in Part 3 of this series. The ssh program is for securely logging into remote machines and executing commands on those remote machines. sftp is a program for performing file transfers over an encrypted ssh connection.
Server Side
On the server side, the core program is sshd, the ssh daemon. The ssh daemon listens for incoming connections from the different client tools. Depending on the type of client tool making the connection, sshd will initiate the appropriate connection and program on the server side.
Conclusion
Computer systems communicate using the SSH protocol all of the time. Since it is such a commonly used protocol, it is helpful to have a better understanding for how it works. While there is much more to the protocol, hopefully this series helps you have a better grasp of SSH.
Articles in the What Exactly is SSH?? (The Secure Shell) Series